Use CI/CD on AWS (CodeCommit + CodeBuild)
In this article, I will try to use the administrator account to setup all necessary components for another IAM user to do all CodeCommit and CodeBuild related tasks. Finally, the IAM user is able to maintain CodeBuild projects with minimal permissions.
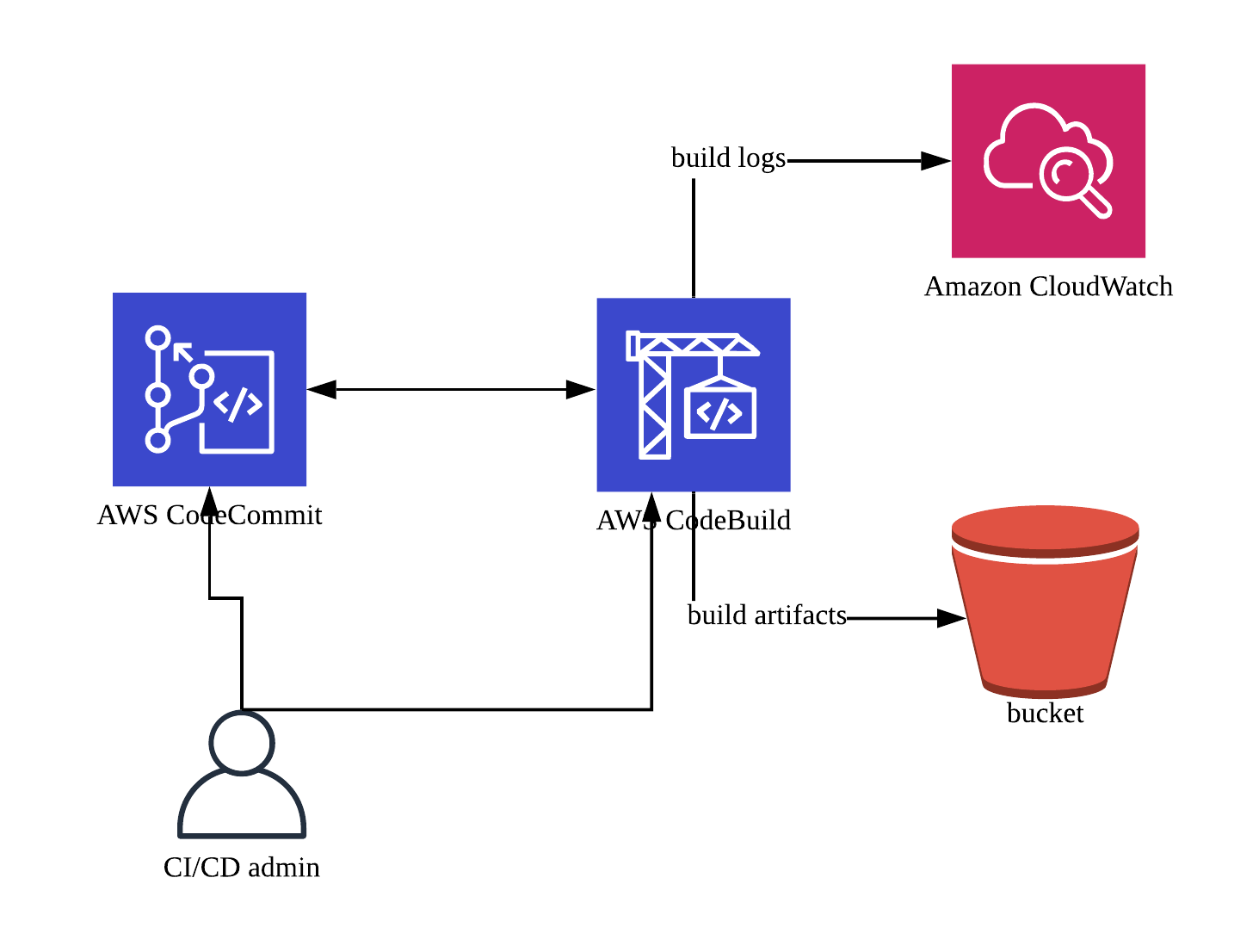
Create below S3 buckets:
- codebuild-artifact-bucket
- codebuild-logs-bucket (if you will copy the build logs to S3)
Create service role for CodeBuild project(s) e.g. CodeBuildServiceRole:
- Use below JSON as inline policy
Inline policy 1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Resource": [
"arn:aws:logs:<REGION>:<AWS-ACCOUNT-ID>:*"
],
"Action": [
"logs:CreateLogGroup",
"logs:CreateLogStream",
"logs:PutLogEvents"
]
},
{
"Effect": "Allow",
"Resource": [
"arn:aws:s3:::codebuild-artifact-bucket",
"arn:aws:s3:::codebuild-artifact-bucket/*",
"arn:aws:s3:::codebuild-logs-bucket",
"arn:aws:s3:::codebuild-logs-bucket/*"
],
"Action": [
"s3:PutObject",
"s3:GetBucketAcl",
"s3:GetBucketLocation"
]
},
{
"Effect": "Allow",
"Action": [
"codecommit:*"
],
"Resource": "*"
}
]
} - Set trusted entities to “AWS service: codebuild”, so that CodeBuild can assume the role.
Create an IAM user to maintain CodeCommit and CodeBuild:
- Add AWSCodeBuildAdminAccess, AWSCodeCommitFullAccess to the user
- Grant the user to pass the role CodeBuildServiceRole to CodeBuild service. An inline policy attached to the user that allows the user to pass the role.
Inline policy 1
2
3
4
5
6
7
8
9
10
11
12
13
14
15{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"iam:GetRole",
"iam:PassRole"
],
"Resource": [
"arn:aws:iam::<ACCOUNT-ID>:role/CodeBuildServiceRole"
]
}
]
} - Assign Console password to allow the IAM user to use AWS Console
- Create HTTPS Git credentials for CodeCommit
Create CodeCommit repository:
- Login with the new IAM user
- Choose Developer Tools > CodeCommit > Repositories
- Click
Create repository - Enter the repository name and description - optional
- Click
Createto create the repository
Create CodeBuild project:
- Login with the new IAM user
- Choose Developer Tools > CodeBuild > Build projects
- Click
Create build project - Enter project name, e.g. codebuild-project1
- Select AWS CodeCommit as source provider
- Choose the repository from the drop down
- Choose Reference Type: Branch, Tag or Commit
- Environment:
- Environment image: Managed image
- Operating system: Ubuntu
- Service role: Existing service role
- Role name: CodeBuildServiceRole
- Uncheck Allow AWS CodeBuild to modify this service role so it can be used with this build project
- Buildspec:
- Build specifications: Use a buildspec file
- Artifacts:
- Type: Amazon S3
- Bucket name: codebuild-artifact-bucket
- Logs (optional):
- CloudWatch:
- CloudWatch logs - optional: Check
- Group name: blank
- Stream name: blank
- S3:
- S3 logs - optional: Check
- Bucket: codebuild-logs-bucket
- CloudWatch:
- Click
Create build projectto create the project