AWS API Gateway notes
Basice Concepts
- REST
REpresentational State Transfer is a software architectural style.- RESTful
A web API that obeys the REST constraints is informally described as RESTful:
- A client-server architecture made up of clients, servers, and resources, with requests managed through HTTP
- Access resources via URI and URL-encoded parameters
- Use of JSON or XML to transmit data.
- Stateless client-server communication
- Cacheable
History of OpenAPI
- In 2011, The Swagger API project was created by Tony Tam
- In 2015, SmartBear Software, the company that maintained Swagger, announced that it was helping create a new organization, under the sponsorship of the Linux Foundation, called the OpenAPI Initiative. A variety of companies, including Google, IBM, and Microsoft are founding members.
- In 2016, the Swagger specification was renamed to OpenAPI Specification, and was moved to a new software repository on GitHub
API Gateway
API Gateway acts as a “front door” for applications to access data, business logic. With AWS Lambda, API Gateway forms the app-facing part of the AWS serverless infrastructure. Amazon API Gateway supports:
- REST (stateless)
PrivatePublic - HTTP (stateless)
Public - WebSocket (stateful)
Public
API endpoint
Edge-optimized API endpoint
For geographically distributed clients. API requests are routed to the nearest CloudFront Point of Presence (POP)1
2
3
4
5
6[root@workflow ~]# ping <api-id>.execute-api.ap-east-1.amazonaws.com
PING yigz4xb0al.execute-api.ap-east-1.amazonaws.com (xx.xxx.xxx.xx) 56(84) bytes of data.
64 bytes from server-XX-XXX-XXX-XX.hkg60.r.cloudfront.net (xx.xxx.xxx.xxx): icmp_seq=1 ttl=245 time=2.69 ms
64 bytes from server-XX-XXX-XXX-XX.hkg60.r.cloudfront.net (xx.xxx.xxx.xxx): icmp_seq=2 ttl=245 time=2.59 ms
64 bytes from server-XX-XXX-XXX-XX.hkg60.r.cloudfront.net (xx.xxx.xxx.xxx): icmp_seq=3 ttl=245 time=2.23 ms
64 bytes from server-XX-XXX-XXX-XX.hkg60.r.cloudfront.net (xx.xxx.xxx.xxx): icmp_seq=4 ttl=245 time=2.46 msPrivate API endpoint (for REST only)
Restricts API access through interface VPC endpoints onlyAccess your private APIs through VPC endpoint:
Create VPC endpoint for API Gateway (execute-api)
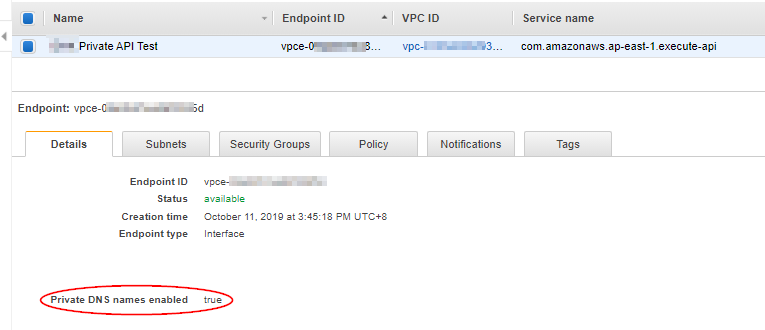
For Security group, select the security group to associate with the VPC endpoint network interfaces.The security group you choose must be set to allow TCP Port 443 inbound HTTPS traffic from either an IP range in your VPC or another security group in your VPC.
To grant access to your VPC endpoint, create a resource policy and attach it to your API:
1
2
3
4
5
6ResourcePolicy:
CustomStatements:
- Effect: 'Allow'
Action: 'execute-api:Invoke'
Resource: ['execute-api:/*/*/*']
Principal: '*'An interface endpoint is an elastic network interface with a private IP address from the IP address range of your subnet. It serves as an entry point for traffic destined to a supported AWS service or a VPC endpoint service. Interface endpoints are powered by AWS PrivateLink.
If you have private DNS enabled (Private DNS is enabled by default), you can use private or public DNS names to access your APIs. If you have private DNS disabled, you can only use public DNS names (i.e. via {vpce-id} ).
- In VPC
1
2
3
4
5
6
7
8
9
10curl -i -X GET \
-H 'x-api-key: xxxxxxxxxxxxxxxxxxx' \
-H "Referer:www.xxxx.com" \
'https://{rest-api-id}.execute-api.ap-east-1.amazonaws.com/Prod/api-test'
curl -i -X GET \
-H "Referer:www.xxxx.com" \
-H 'x-api-key: xxxxxxxxxxxxxxxxxxxxxxxx' \
-H "Host: {rest-api-id}.execute-api.ap-east-1.amazonaws.com" \
'https://{vpce-id}.execute-api.ap-east-1.amazonaws.com/Prod/api-test'
- In VPC
Controlling access to API Gateway APIs
API keys – API keys are alphanumeric string values that you distribute to application developer customers to grant access to your API.
Only the AWS::Serverless::Api resource type supports API keys.
Regional API endpoint
A regional API endpoint is intended for clients in the same region.
Summary of endpoint and accessibilty
| Endpoint type | In VPC with ENI with Enable Private DNS Name |
Outside VPC |
|---|---|---|
| Edge |
|
|
| Regional |
|
|
| Private |
|
None |
Common Serverless Resources
AWS::Serverless::Function
Type: AWS::Serverless::Function
Properties:
ApiEvent:
Type: Api
Properties:
Method: get
Path: /group/{user}
RestApiId:
Ref: MyApi
RestApiId
- Identifier of a RestApi resource, which must contain an operation with the given path and method. Typically, this is set to reference an AWS::Serverless::Api resource defined in this template. If you don’t define this property, AWS SAM creates a default AWS::Serverless::Api resource using a generated OpenApi document. That resource contains a union of all paths and methods defined by Api events in the same template that do not specify a RestApiId
AWS::Serverless::Api (REST)
Type: AWS::Serverless::Api |
AWS::Serverless::HttpApi
Type: AWS::Serverless::HttpApi |
AWS::Serverless::Function
Global section |
Validating AWS SAM template files
sam validate <path-to-file>/template.yml |
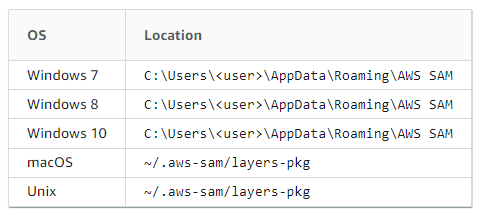
Working with layers
When you invoke your function using one of the sam local commands, the layers package of your function is downloaded and cached on your local host.